The “Islamic State Hacking Division” is urging terrorists to use the names, emails, passwords, locations and phone numbers of hundreds of U.S. military and government officials it apparently accessed to carry out lone wolf attacks.
Islamic State supporters tweeted a link to a massive document with information it claims are personnel data of more than 1,482 members of the U.S. military, NASA, the FBI, the Port Authority of New York and New Jersey, and the State Department, along with messages like:
“We call all #LoneWolves in US and Countries where US Diplomats are working to Process this Info & Assassinate” said one message, along with personal details of a soldier in Alabama, reported Vocativ. Another tweet shared information claiming to be the personal details of a staff member from the U.S. embassy in Cairo and said: “To the lone wolves of Egypt.”

The document itself warns:
“O Crusaders, as you continue your aggression towards the Islamic State and your bombing campaign against the muslims, know that we are in your emails and computer systems, watching and recording your every move, we have your names and addresses, we are in your emails and social media accounts, we are extracting confidential data and passing on your personal information to the soldiers of the [Caliphate,] who soon with the permission of Allah will strike at your necks in your own lands!”
The purported Twitter account of infamous British Islamic State hacker Abu Hussain al-Britani posted a link with the information. He tweeted: “They have us on their ‘hit list’, and we have them on ours too…” Al-Britani, whose real name is Junaid Hussein, was convicted and imprisoned in 2012 for hacking then-Prime Minister Tony Blair’s personal information.
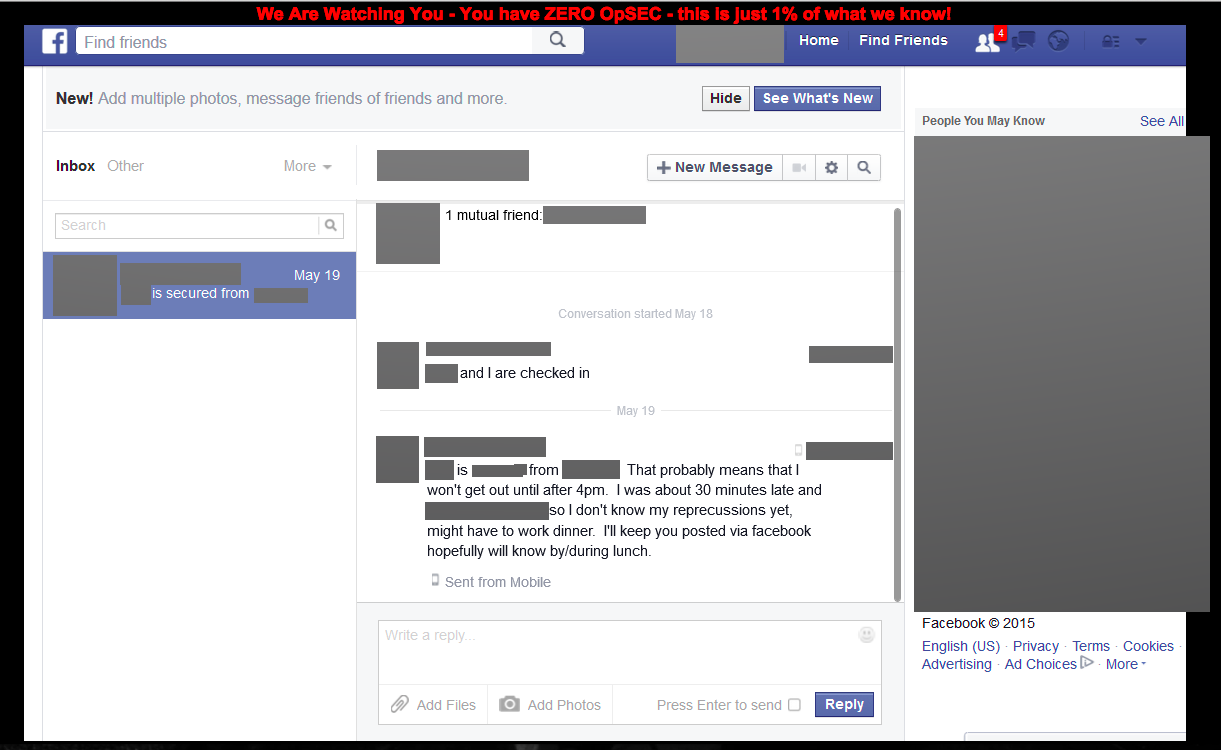
At the bottom of the leaked document, originally posted on zonehmirrors.org, are receipts from State Department employees along with their credit card numbers. There are also several screencaps of purported private Facebook messages between U.S. military members along with the warning:
“We Are Watching You — You have ZERO OpSEC [operational security] — this is just 1% of what we know!”
The “Islamic State Hacking Division” account tweeted about the list: “Looks like the FBI/CIA still cant remove it from the internet :).”
State Department employees comprise about a quarter of the alleged personal information on the list.
“The information in this targeting list is extremely valuable,” said Alice Kassirer, an analyst with FlashPoint Global Partners, a security intelligence firm.
The Islamic State claims it obtained the information from military computers, which is highly unlikely, given the variety of the data in the list, Kassirer said. It does not appear the information came from one centralized breach, as the Islamic State claims, and it may have been culled together from social media accounts, as was the case with previous lists the Islamic State has released.
“We have not yet been able to authenticate the source,” she said. She pointed out that one of the targets on the bottom of the list was an employee at Wells Fargo five years ago, so at least some of the information on the list is out-of-date.
The Defense Department has not confirmed the origins or authenticity of the list. Army Chief of Staff Gen. Ray Odierno said during a press conference Wednesday that he has not “seen the lists myself” but “this is the second or third time they’ve claimed that and the first two times I’ll tell you, whatever lists they got were not taken by any cyber attack.”
The list also contains the alleged personal information of members of U.S. Central Command, the FBI, U.S. city officials, the British Embassy, the Federal Trade Commission, the National Institute of Standards and Technology, and employees of Wells Fargo.
The Washington Examiner confirmed that portions of the private information posted appear to be accurate, while other information is either inaccurate or out-of-date.
Islamic State hackers can buy techniques, strategies and hacking information on the dark web at low cost, so a document like this would not be difficult to assemble, said Bill Stewart, executive vice president of Booz Allen Hamilton’s cybersecurity division.
“Organizations like the Islamic State have capabilities that are not difficult to obtain in the open market because the barriers to entry … have gone down drastically over the last couple of years,” Stewart said.
“I don’t know for a fact what was leveraged to get this, but in most cases if you pull back the layers of the onion you find a group like this, that has some smart people that are motivated and that have a cause, they’re going to find the quickest, easiest way to make things happen and part of that is on the dark web,” Stewart said. “Exactly how they did this I can’t comment on, but a typical situation today is through a combination of several things and the easiest way to do it is … through the people, not the technology.”
Stewart said hacks typically occur through one of two ways: either low-level employees have done something outside of policy, like using social media improperly, clicking on a link in a phishing email, or downloading something they should not have; or the institution has not routinely or uniformly kept patches up-to-date and has not been investigating for signs of breaches.
“Most breaches occur for 180 days before anyone finds it,” Stewart said. “The U.S. government is very good at automation, but their challenge is that they leave a huge footprint.”
“We’re going to be seeing a lot more” cyber attacks like this one, Kassirer said, given the growing sophistication of the jihadi hackers. “The guys are a lot younger; a lot more tech savvy.”
As to the origin of this hack, she said, “all of the possibilities are still on the table.”
Jacqueline Klimas contributed to this report.
